As mentioned previously, working with a bridge really should prevail over this concern.
In the past, this was relatively intricate, but is a large amount simpler in the latest version. You are going to need to have to very first identify a bridge and then configure it with the Tor browser. Does Tor actually make you anonymous?It’s pretty challenging, if not not possible, to develop into genuinely anonymous on the internet, but Tor can unquestionably support you get there.
- Can i kick gadgets away my circle
- How to take care of tools linked to my wireless
- Can i unblock my Ip
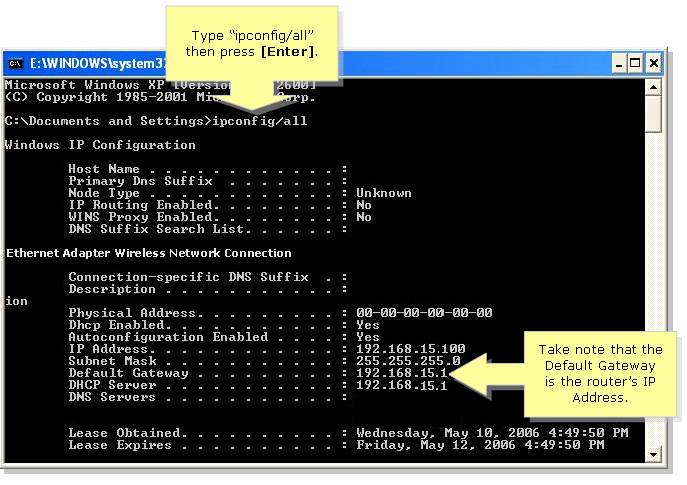
- Ways to get a hold of my network system Identification IP address
- Just what is world Ip address and local Ip address
All of your visitors arriving at its vacation spot will surface to appear from a Tor exit node , so will have the IP handle of that node assigned to it. Because the traffic has handed by means of various more nodes whilst encrypted, it https://check-my-ip.co/ are unable to be traced back again to you. However, one of the issues lies in trusting the operator of the exit node. If you happen to be visiting an unencrypted (non-HTTPS) site, it’s achievable the node operator can track your action and look at your information.
Can two pcs have a similar Ip
They could accumulate data these types of as which webpages you happen to be viewing, your login info, the material of your messages or posts, and the searches you complete. Despite the fact that, there’s no way to trace that information back to you or even back again to the entry node. It’s really worth noting that using the Tor browser only safeguards traffic going through that relationship and will never anonymize other apps on your computer (although quite a few can be configured to the Tor community by way of other means). Also, your ISP can however see that you’re utilizing Tor.
How can you get a hold of my Ip for my Wi-fi
For enhanced privacy, you can use a VPN together with the Tor browser. What is the darknet and how is Tor similar to it?If you might be familiar with the time period, the “clear internet”, you are going to know that it refers to the part of the world-wide-web that can be freely accessed, that is with out Tor or an alternate browser. On the other side you have the deep web.
Can my IP address be greatly improved
- Who owns the Ip
- How can i strike another person away my Wi-fi TP Weblink
- Should you kick someone out your Wireless
- How can you view exactly how many products are connected to your WIFI
This includes information that isn’t really indexed by research engines, such as outdated articles, non-public files, and net pages that have barred look for engines from crawling them. Also within the deep world wide web is the darknet. This content can usually only be accessed working with particular applications like Tor.
The darknet houses some legit web-sites, but it is much better known for becoming a location rife with illicit exercise. You can entry the distinct net with Tor, but you can also accessibility darknet internet websites, specifically . onion internet sites.
These are web-sites which only men and women working with the Tor browser can access, and have . onion as section of their URL. They are also referred to as “Tor hidden providers. “They’re not indexed by lookup engines and can be challenging to uncover if you you should not know in which to glimpse. Tor shields the anonymity of the operators of .
onion web sites, so it would be tough to find out who is managing them. Of training course, the mix of the two operator and user anonymity is what helps make the darknet best for felony activity. That being reported, there are loads of legitimate web-sites that have . onion versions. For illustration, VPNs are geared toward privateness-aware consumers and some offer you . onion versions of their internet site, ExpressVPN remaining 1 instance.
You can even established up a . onion site of your individual via the Tor browser.
Why would somebody want to use Tor?As talked about, Tor is normally associated with unlawful action and consumers wanting to entry the dark internet.
